Introduction: Exploring the need for an Active Directory Domain Controller and Server Security Audit
It’s no secret that cybercrime is on the rise. As technology advances, so do the methods of malicious actors. With increasing numbers of businesses relying on digital systems to manage their data, companies must ensure their systems are secure. An active directory domain control and server security audit are critical components of a particular system.
An active directory domain control and server security audit are designed to identify potential security vulnerabilities in an organization’s network infrastructure. It can also help detect malicious activity or suspicious behavior within a network environment. In addition to identifying potential threats, the audit can provide valuable insight into how an organization’s security posture could be improved.
The need for a comprehensive security audit has never been greater. As cyber criminals become more sophisticated, the ability of organizations to protect their networks from attack becomes increasingly tricky. Organizations can ensure that their networks and data remain secure by conducting a regular security audit.
The need for a comprehensive security audit has never been greater. As cyber criminals become more sophisticated, the ability of organizations to protect their networks from attack becomes increasingly tricky. Organizations can ensure that their networks and data remain secure by conducting a regular security audit.
At its core, an active directory domain control and server security audit should include the following steps:
-
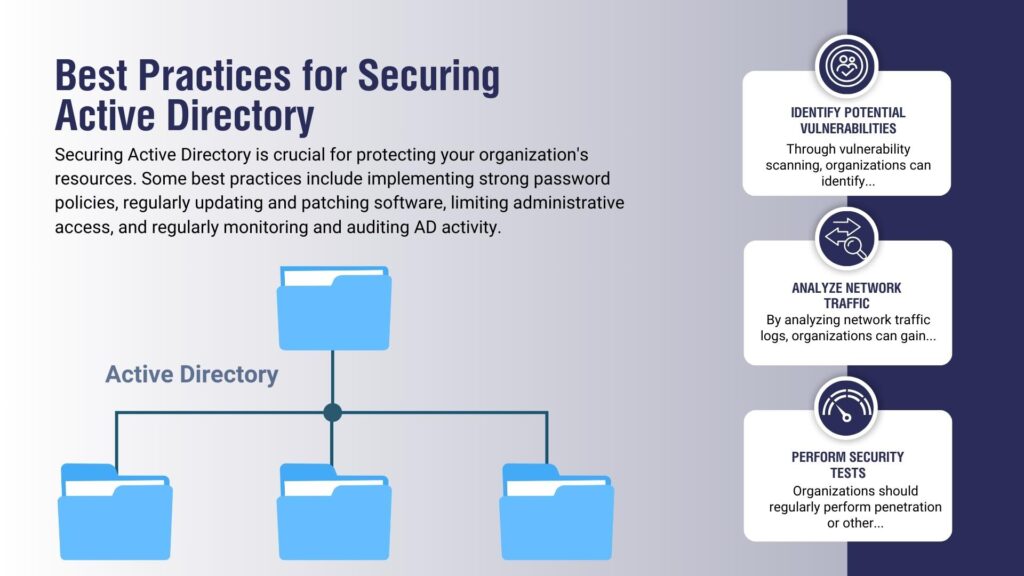
- Identify Potential Vulnerabilities:
Through vulnerability scanning, organizations can identify potential weaknesses in their network infrastructure that attackers could exploit. - Analyze Network Traffic:
By analyzing network traffic logs, organizations can gain insight into traffic entering and leaving their networks and any suspicious activity within the environment. - Perform Security Tests:
Organizations should regularly perform penetration or other security tests to assess how well their networks are protected from attack.
- Identify Potential Vulnerabilities:
When it comes to protecting your organization from cyber attacks, knowledge is power,
A comprehensive active directory domain control and server security audit can give organizations the knowledge they need to protect themselves from cyber threats. Organizations can ensure that they remain protected from malicious actors by taking proactive steps to identify potential vulnerabilities in their systems and implementing measures to mitigate those risks.
The Time For Action Is Now!
Don’t wait until it’s too late – now is the time for organizations to take action by performing an active directory domain control and server security audit. Doing so will ensure that your networks and data remain secure.
The Dangers of Ignoring Active Directory Security: What You Don’t Know Can Hurt You

Active Directory Domain Control and Servers are the backbone of any organization’s network infrastructure. But these systems need to be adequately secured. In that case, they can become a gateway for cyberpunks to gain access to critical data, disrupt operations, and even launch attacks on other systems. This is why conducting regular security audits on these systems is so important. It’s no secret that cyber-attacks are becoming more sophisticated and persistent every day, and organizations need to stay ahead of these potential threats. A security audit for Active Directory Domain Control and Servers can help identify any weaknesses in your system that malicious actors could exploit. It will also ensure that all user accounts are up-to-date and secure and provide an overview of your system’s overall security posture. Unfortunately, many organizations don’t take the time or resources to properly audit their Active Directory Domain Control and Servers. This can lead to significant consequences if a breach occurs due to a lack of proper security measures. Not only will it cost the company money in terms of repairs and lost data, but it could also damage its reputation with customers or partners. Ignoring the need for regular security audits is simply negligent; at worst, it could be disastrous. Organizations must take energetic steps now to protect their networks from potential threats before they become a reality. Investing in a comprehensive security audit for Active Directory Domain Control and Servers is one way to ensure that your organization is taking all necessary precautions against cyber-attacks. The bottom line is this: what you don’t know CAN hurt you! Don’t wait until it’s too late – invest in a thorough security audit for your Active Directory Domain Control and Servers today!
Users Account and Access Control: Ensuring Properly Authorized Access to Data and Resources
Organizations are increasingly vulnerable to malicious cyber-attacks and data breaches. Now more than ever, it’s essential to have proper authorization protocols in place. This is especially true for Active Directory Domain Controllers (ADDCs) and servers, which can contain sensitive data and resources. To protect your company’s data and resources, you must conduct a security audit of your ADDCs and servers. A security audit of your ADDCs and servers will help you identify any vulnerabilities in your system and any user accounts or access control issues that could open you to attack. Ensuring that only suitably authorized users have access to the data and resources within these systems is essential. A thorough security audit will allow you to identify any unauthorized users or accounts that may be present on the system, as well as any weak password policies that malicious actors could exploit. It is also essential to evaluate the security protocols for managing user accounts and access control. This includes reviewing the authentication methods, such as two-factor authentication, and the authorization policies for granting access to various resources.
Additionally, it is vital to ensure that all user accounts are correctly configured with appropriate privileges so they can only access the necessary data or resources. In today’s digital age, protecting your organization from malicious actors requires staying one step ahead of them. A thorough security audit of your ADDCs and servers can help ensure that only those properly authorized users can access delicate data and resources within these systems. Don’t let what you don’t know hurt you—it’s time for a security audit!
Password and Authentication Policies: Establishing Guidelines of Strong Credentials

In the age of cyber threats becoming increasingly polished, companies must stay ahead of the game and ensure their security systems are robust enough to protect their data. One area often overlooked in security audits is the authentication policies established for Active Directory Domain Control and Servers. Organizations must have strong password and authentication policies to protect sensitive information from malicious actors. Organizations should start by setting up password requirements that are both secure and difficult to guess. This includes requiring passwords to be at least eight characters long, contain a combination of numbers, special symbols, and upper-case letters, and be changed regularly.
Additionally, implementing two-factor authentication adds an extra layer of protection by asking the end users to provide additional information beyond just their credentials when they attempt to log into an account. Organizations can also ensure that users are not reusing passwords across different versions or sharing them with others. Single sign-on (SSO) solutions can help reduce the risk of credential theft by providing users with one set of credentials for multiple applications or services. This eliminates the need for users to remember numerous passwords and reduces the risk of weak or reused credentials being used across different accounts. It is also crucial for organizations to monitor user access regularly to detect any suspicious activity or unauthorized access attempts. Organizations should periodically review logs for any unusual user activity or failed login attempts, as these can indicate potential malicious activities such as brute force attacks or credential stuffing attacks.
Additionally, organizations should keep track of who has administrative privileges on their systems so they know who has access to sensitive data if any unauthorized changes occur. The importance of strong password and authentication policies must be recognized. Taking proactive steps now can help protect your organization from potential cyber threats down the line – so don’t wait until it’s too late!
Security Event Logging: Tracking System activity for Early Detection of threats
We live in an age where cyber threats are becoming more sophisticated and pervasive, making it increasingly crucial for businesses to protect their networks from malicious actors. While long-established security measures such as firewalls and antivirus software can help to keep your system safe, they are not foolproof. That is why organizations must regularly conduct security audits of their Active Directory Domain Controllers (ADDCs) and servers to ensure that all systems are secure. Security event logging is one of the most effective ways to detect potential threats. This process involves tracking the activity of users and services on a system to identify any suspicious behaviour or anomalous activity. By doing so, organizations can gain insight into who is accessing their plans, what they are doing there, and how long they have been present. This allows them to identify suspicious activity indicating a potential breach or attack quickly. Security event logging also provides an additional layer of defence against malicious actors by enabling organizations to track user access over time. By monitoring user logins and other system activities, administrators can detect when someone has gained unauthorized access or attempted to tamper with sensitive data. This allows them to take swift action if necessary, minimizing the damage caused by any potential attack or breach. The importance of security event logging must be balanced; organizations must have an up-to-date record of all user activities to protect their systems from external threats. With suitable appliances/tools and processes, associations can gain invaluable insight into who is accessing their networks and what they are doing there – information that can be used to catch potential dangers before they become a severe problem. It is clear that regular security audits are essential for protecting ADDCs and servers from cyberattacks; however, with the right tools in place, organizations can establish a robust system that will help them identify potential threats before it’s too late. By implementing comprehensive security event logging processes, businesses can stay one step ahead of vicious actors – ensuring their networks remain secure now and in the future.
Security Group and Role Management: Understanding Permission Across the Network
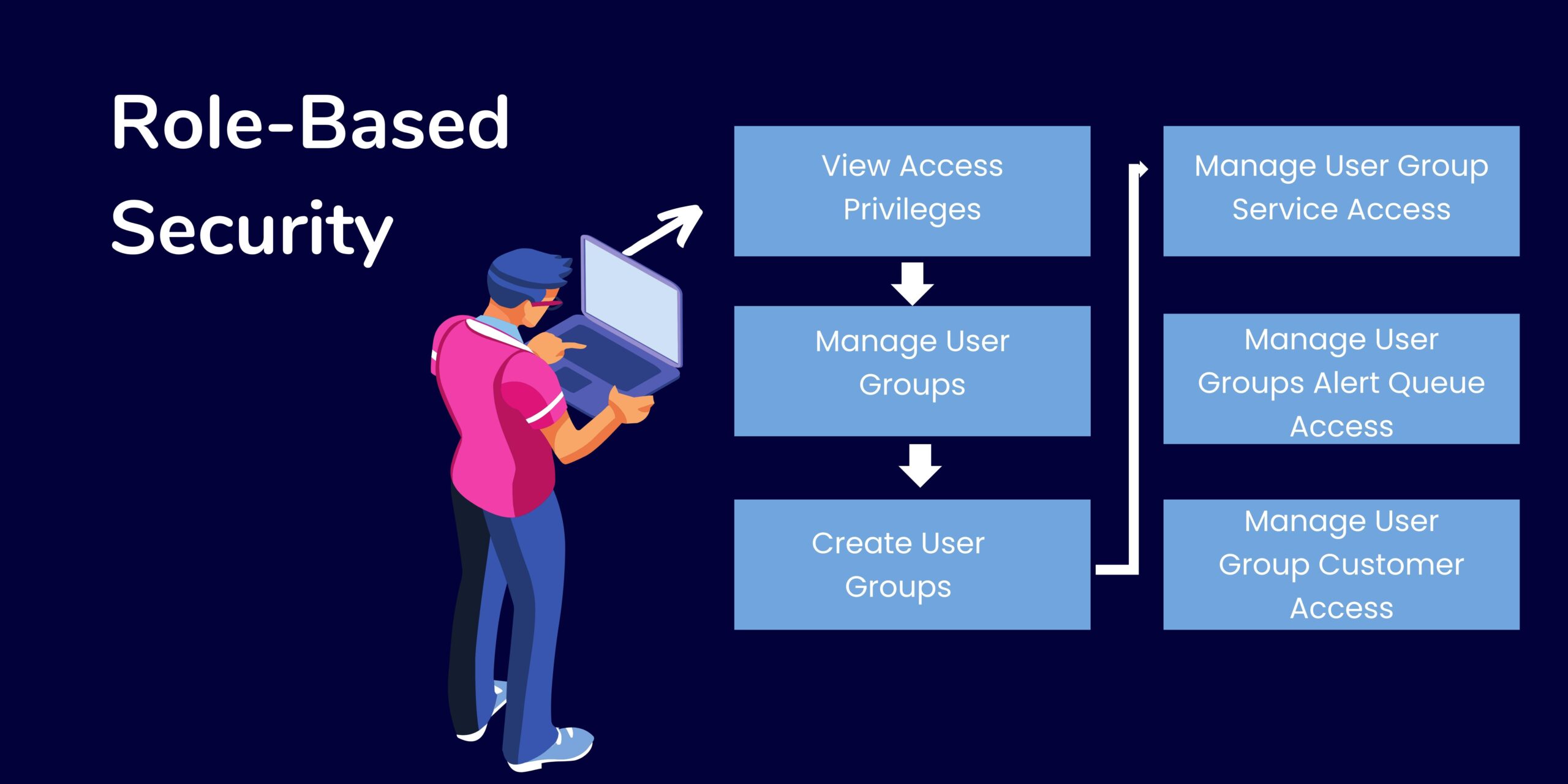
As cyber threats become increasingly sophisticated, organizations must increase their efforts to protect their data and systems. One way to do this is through regular security audits of Active Directory domain controllers and servers. While it may seem unnecessary, the potential risks of not doing a thorough security audit can be disastrous. It’s essential to understand the permissions granted across your network. Without proper security group and role management, malicious actors could gain access to sensitive information or disrupt operations. Unfortunately, many organizations don’t realize the importance of adequately managing permissions until it’s too late. It would be best to regularly audit your Active Directory domain controllers and servers to protect your organization from potential cyber threats. This process should examine user accounts, groups, roles, policies, and other settings to ensure appropriate access levels. It should also include monitoring for any suspicious activity or unauthorized changes. Keeping up with the latest cutting-edge security technologies can help miscalculate the risk of a security breach in your organization. However, it’s equally important to remember that what you don’t know can hurt you. A thorough security audit will ensure that your network is secure and safeguarded against possible threats.
Audit Trail and Monitoring: Keeping Track of Who has accessed What
It is no secret that the digital world is constantly evolving and expanding. As such, keeping up with security protocols and ensuring that your organization’s servers and domain controllers are secure from malicious actors is ongoing. One of the most essential steps in this process is conducting a security audit for Active Directory Domain Control and Servers. An audit can be performed manually or automated, depending on your preferences. Still, either way, it ensures that all user accounts, network accesses, and system configurations have been appropriately configured and secured. This includes monitoring which users have accessed what files or programs and ensuring that any system changes have been adequately documented. Audit trails are essential in determining who has accessed what on a network or server; they provide an objective record of changes to the system configuration or user access privileges. In addition to audit trails, organizations should consider implementing a monitoring system to keep tabs on user activity within the domain. This could include logging all attempts to access restricted files or programs and track which users have logged into the system at any given time. By conducting regular security audits for Active Directory Domain Control and Servers, organizations can ensure that their systems remain secure from threats and malicious actors. Additionally, having an audit trail and monitoring system will give organizations greater visibility into who has accessed what on their networks or servers. The urgency of this type of security cannot be understated – not only will it protect your organization from potential cyberattacks and help you stay ahead of the cutting-edge digital landscape we live in today.
Firewall and Network Security: Stopping Unauthorized Traffic from Entering the Network
The need for an active security audit of your Active Directory domain controllers and servers must be recognized. In the digital age, every organization is vulnerable to cyber-attacks, and the consequences of a breach can be devastating. By taking proactive steps to secure your network from unauthorized traffic, you can prevent malicious actors from infiltrating your system and stealing confidential data. Firewall and network security are essential elements in any organization’s security plan. A firewall acts as a barrier between your internal network and the public internet, blocking unwanted traffic from entering while allowing legitimate requests to pass through. Firewalls are also invaluable in monitoring network activity, allowing administrators to detect suspicious activities before they become a significant threat. To prevent unauthorized access to your system, cutting-edge technologies such as intrusion detection systems (IDS) and intrusion prevention systems (IPS) are essential tools. These systems monitor incoming traffic for signs of malicious activity and can block access if necessary.
Additionally, organizations should consider deploying advanced endpoint protection solutions that can detect malware or malicious code before it has a chance to spread throughout the network. The time has come for organizations to take their security seriously by conducting regular security audits on their Active Directory domain controllers and servers. Doing so will help identify potential vulnerabilities in the system before malicious actors can exploit them. It is also essential that organizations keep their software up-to-date with the latest patches and updates to reduce the risk of attack. Taking these measures now will ensure that your organization remains protected against potential threats in the future.
Data Backup and Disaster Recovery: Preparing for a Worst case scenario
Data is the lifeblood of any business, and with the rise of cybercrime, companies must take proactive steps to protect their data. One such measure is conducting regular security audits on Active Directory domain controllers and servers. A security audit helps identify potential weaknesses in an organization’s system, allowing IT administrators to rectify them before they become problematic. But what about data backup and disaster recovery? It’s often overlooked in security audits, yet it’s equally as important as any other aspect of IT security. After all, if a disaster strikes or a system failure occurs, a reliable backup plan can make all the difference between recovering quickly or dealing with lengthy downtime and lost data. The key to thriving disaster recovery is having a practical backup plan covering all system aspects. This means ensuring that all systems are backed up regularly and that backups are stored securely offsite (preferably in the cloud). That redundant backups are available should one become corrupted or lost.
Additionally, organizations should have processes in place to ensure regular testing of backups so they can be sure they can recover their data if needed. Organizations must understand the importance of data backup and disaster recovery when protecting their information from cybercriminals. A comprehensive security audit should include checks for these areas—and any identified risks should be addressed immediately. Don’t let what you don’t know hurt you; ensure your organization is prepared for worst-case scenarios by conducting regular security audits and implementing robust backup plans today.
Vulnerability Assessment and Penetration Testing: Identifying Potential Weakness Before Attackers Do
The security of your organization’s Active Directory Domain Control and servers is paramount. As cyber attackers become more sophisticated, you must stay ahead of the competition by proactively determining vulnerabilities before they can be exploited. Vulnerability assessment and penetration testing are two key components to help ensure your systems are secure. Vulnerability assessments are designed to identify potential weaknesses in your system, such as out-of-date software or inadequate user access control settings. Penetration testing goes one step further by exploiting those vulnerabilities to gain unauthorized access, which can provide invaluable insight into potential threats posed to your network. These two tests can help you better understand and mitigate your security risks. Organizations must take the time to assess their security posture continuously. This includes performing regular vulnerability assessments and penetration tests and implementing best practices such as patch management, user access control, network monitoring, and application-allow listing. By staying on top of potential threats and taking proactive steps to protect yourself from them, you can help ensure that your sensitive data remains safe from malicious actors. Take your time with your organization’s security – invest in an audit for Active Directory Domain Control and servers today! Doing so can provide peace of mind knowing that you are protected against potential threats before they become a reality.
The Urgency of a Security Audit for Active Directory Domain Control and Servers
As technology continues to evolve, so do the threats that come with it. While many organizations know the importance of cybersecurity, many still need to learn of the risks their Active Directory Domain Control and Servers pose. The truth is that without an audit of these systems, you may be vulnerable to cyber-attacks and data breaches. The urgency of performing a security audit must be balanced. With the right tools and processes in place, you can identify potential weaknesses in your network and take steps to prevent them from becoming real threats. It is also essential to update your systems regularly, as new vulnerabilities may arise anytime.
Furthermore, an audit will help you identify any unauthorized access to your data or systems and any suspicious activities that may be taking place on your network. This information can then be used to strengthen your security posture and ensure that all users have appropriate access levels for their roles within the organization. The bottom line is this: when it comes to security audits for Active Directory Domain Control and Servers, don’t wait until it’s too late – act now! Taking proactive measures will help protect your business from costly data breaches and cyber-attacks in the future.